Fortigate – Adjustments made on the Microtic side during the final stage of IPSEC VPN configuration between Mikrotik consist of NAT and IPSEC sections.
Nat creation first
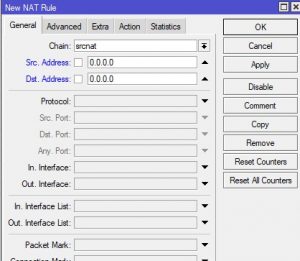
Ip -> FIREWALL -> Nat tab creates a new rule and determines the source and destination address blocks with the srcnat option.
The IPSEC phase completes in 3 steps;
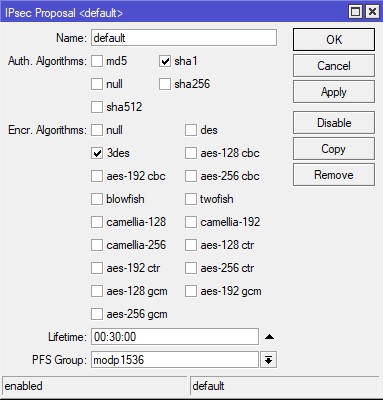
- In phases, we create a new Proposal with the following details on the IP -> IPSEC -> Proposal tab.
In Phase 2, the IP -> IPSEC ->Peer tab enters the WAN ip address of the party we will create the new Peer and vpn as follows.
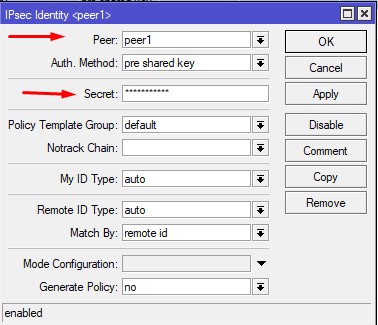
Phase 3 new IPSEC identity is created on the IP -> IPSEC ->Identities tab. Peer1, which we created in peer, is selected. The password we enter on the Fortigate side is entered in this field at this stage.
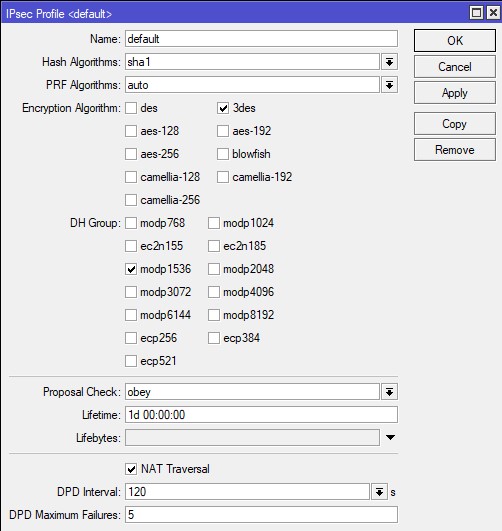
In Phase 4, the IP -> iscreated into the new IPSEC Profile on the IPSEC -> Profiles tab. The encryption method we set out on the Fortinet side is applied in this field.
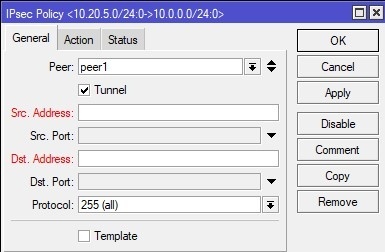
5. In the final stage, new IPSEC Police is created on the IP -> IPSEC -> Policies tab.
If everything is fine with the latest actions, we see that the following link has been established in the status tab of the Policies that we have created
In the same way, we can verify that the connection is established in the IPsec Monitor section under the Monitor menu on the Fortigate side